30DaysMSGraph – Day 9 – Azure AD applications on V2 endpoint
List of all posts in the #30DaysMSGraph series
-Today’s post written by Srinivas Varukala
In Day 8 we discussed the authentication roadmap and access tokens which are crucial to make Microsoft Graph requests. Today we’ll look at registering an Azure Active Directory (Azure AD) application that will be used to communicate with Microsoft Graph.

Before we dive into the steps for registering an Azure AD Application, let us clarify few things. There are two endpoints in Azure AD to register applications, called V1 and V2. In this post we are going to use a preview of the new experience Azure AD app registration portal and the V2 endpoint to register the application as that is the recommended approach moving forward. See below diagram adapted from Day 8 future state roadmap with highlighted boxes on the components for today’s focus. On Day 10, we will show how to register app using V1 endpoint. Please visit the article on Comparing the Azure AD v2.0 endpoint with the v1.0 endpoint to learn about the differences between these endpoints. For this article we are going to use Azure AD V2.0 endpoint.
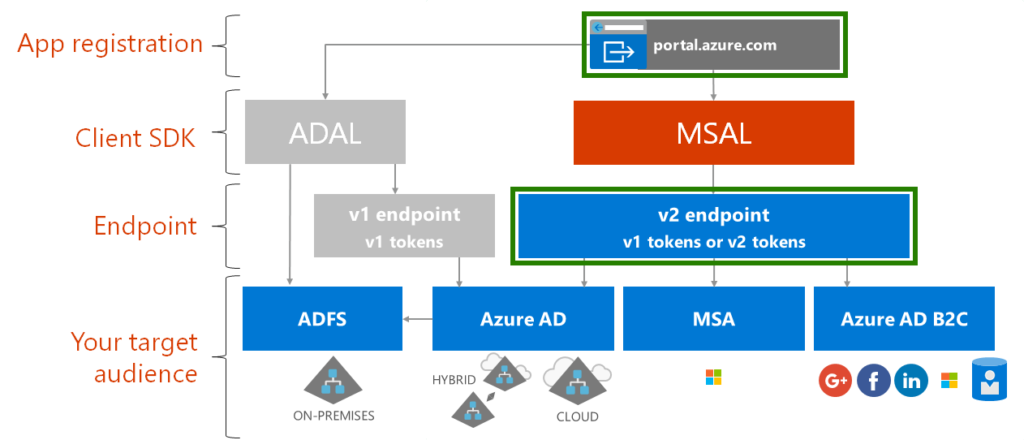
Registering the Azure AD V2 App using Azure AD App Registration (GA as of May 2019)
Open a browser and navigate to the App registrations in Azure AD Portal.
Note: All information and example screenshots are using the preview versions of this registration portal and are subject to change. We will attempt to update this documentation to match after the portal is generally available (GA). Read more about the New App registrations experience now in public preview.
Note: Read more about the New App registrations experience is now generally available.
Click + New registration from the current blade content.

On the Register an application page, specify the following values:
- Name = msgraph-clientcred-app (or any name that works for you)
- Supported account types = <choose the value that applies to your needs>
- Redirect URI = Web : https://localhost:8080
Note: The Redirect URI value can be changed later and can also be pointed at a URI that isn’t actually hosted.

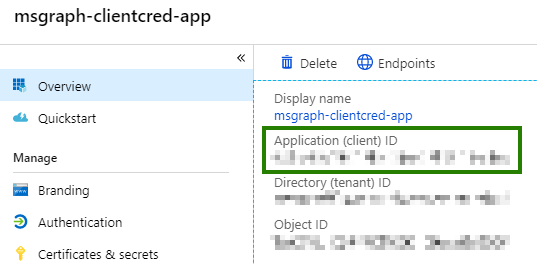
Click “Register” button to register the application. After the app is created you will be directed to the application Overview page. On this page, copy the Application (client) ID and Directory (tenant) ID as you will need them later.
Select Authentication from the current blade navigation pane. Add the URI https://app.getpostman.com/oauth2/callback as the second redirect URI and click Save. We will use this URL when calling Microsoft Graph using Postman at a later day .

- Select Certificates & Secrets from the current blade navigation pane.
- Select New client secret.
- On the Add a client secret dialog, specify the following values:
- Description = Secret1
- Expires = In 1 year
- Click Add

After the screen has updated with the newly created client secret, copy the VALUE of the client secret as you will need it later.
Important: This secret string is never shown again, so make sure you copy it now.

The next step is to set the required permissions to the application to make the Microsoft Graph calls. We will discuss application permissions in more detail on Day 11, but for today understand that there are two categories of permissions:
- Delegated Permissions
- Use these permissions when the application runs under the user context. In this case, we are delegating the application to run on behalf of the user.
- Application Permissions
- Use these permissions when using client-credential flow (also called app only flow). In this case, the application executes without any user context.
- We are adding an application permission in this post.
In a later post we will use the Azure AD Application created in this post to make Microsoft Graph query to list all users in the organization. Accordingly we will add “User.Read.All” application permission.
Click API permissions in the current blade navigation pane. Click on the + Add a permission button. Select Microsoft Graph. Select Application Permissions. Expand the User category and check the box for User.Read.All permission.
Note: You will see that the Admin consent required column shows as Yes. This means the Azure AD Admin must grant the permissions before the application can be used to make Microsoft Graph queries.

Back on the API Permissions screen click Grant admin consent for <tenantName>, then click Yes.

Note: You must be a domain administrator for Azure AD or similar role in order to grant admin consent. If you do not have appropriate permissions stay tuned for a topic in Day 11 that offers an alternative permission level.
Try It Out
Navigate to the App registrations. Walk through these steps to create an app, assign it permissions, and grant admin consent.
- Create a new Azure AD application.
- Assign the delegated permission for Mail.Read.
- Assign the delegated permission for Calendars.ReadWrite.
- Assign the application permission for User.Invite.All.
- Grant admin consent to the application.
Join us tomorrow as we register an Azure AD application with the V1 endpoint in Day 10.

 Light
Light Dark
Dark